My Accomplishments
Certifications arranged in chronological order. Hover to reveal skills & knowledge.
◀ Cards scroll automatically • Hover to pause • Flip cards to see details ▶

Skills & Knowledge
- Active Directory Enumeration & Exploitation
- Offensive Python
- Linux & Windows Privilege Escalation

Skills & Knowledge
- Advanced Exploitation: SQL Injection, RFI, SSH Tunneling
- Buffer Overflow Exploitation
- Basic Active Directory Exploitation

Skills & Knowledge
- Assessment Methodologies
- Web Application Penetration Testing
- Host & Networking Penetration Testing

Skills & Knowledge
- Client Side Attacks
- Web Exploitation
- Tunneling
- Privilege Escalation
- Active Directory Attacks

Skills & Knowledge
- Active Directory Enumeration
- Local Privilege Escalation
- Domain Privilege Escalation
- Domain Persistence
- Cross Trust Attacks
- Inter-forest Trust Attacks
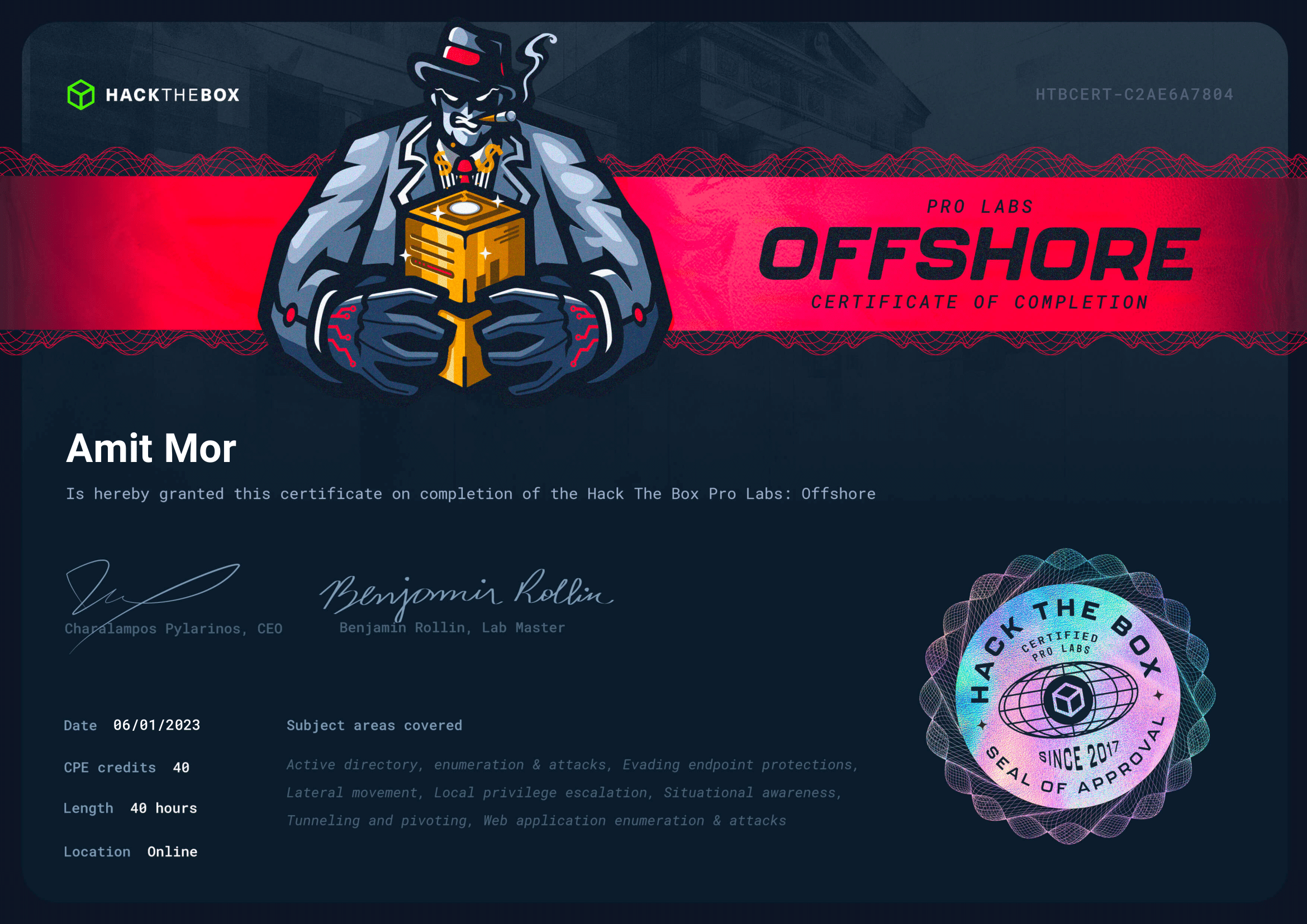
Skills & Knowledge
- Web Application Attacks
- Enumeration
- Real-World Active Directory Flaws
- Lateral Movement & Trust Boundaries
- Evading Endpoint Protections
- Reverse Engineering

Skills & Knowledge
- Client-Side Attacks
- Process Injection & Migration
- Antivirus Evasion
- Application Allow-Listing Bypass
- Network Filter Bypass
- Lateral Movement (Win/Linux)
- Microsoft SQL Attacks

Skills & Knowledge
- Persistent XSS & Session Hijacking
- File Upload/Extension Bypasses
- PostgreSQL Extensions & UDFs
- Type Juggling & Magic Hashes
- Blind SQL Injection
- CSRF & REGEX Bypasses
- .NET Assembly Debugging

Skills & Knowledge
- Active Directory Enumeration & Exploitation
- Offensive Python
- Linux & Windows Privilege Escalation

Skills & Knowledge
- Advanced Exploitation: SQL Injection, RFI, SSH Tunneling
- Buffer Overflow Exploitation
- Basic Active Directory Exploitation

Skills & Knowledge
- Assessment Methodologies
- Web Application Penetration Testing
- Host & Networking Penetration Testing

Skills & Knowledge
- Client Side Attacks
- Web Exploitation
- Tunneling
- Privilege Escalation
- Active Directory Attacks

Skills & Knowledge
- Active Directory Enumeration
- Local Privilege Escalation
- Domain Privilege Escalation
- Domain Persistence
- Cross Trust Attacks
- Inter-forest Trust Attacks

Skills & Knowledge
- Web Application Attacks
- Enumeration
- Real-World Active Directory Flaws
- Lateral Movement & Trust Boundaries
- Evading Endpoint Protections
- Reverse Engineering

Skills & Knowledge
- Client-Side Attacks
- Process Injection & Migration
- Antivirus Evasion
- Application Allow-Listing Bypass
- Network Filter Bypass
- Lateral Movement (Win/Linux)
- Microsoft SQL Attacks

Skills & Knowledge
- Persistent XSS & Session Hijacking
- File Upload/Extension Bypasses
- PostgreSQL Extensions & UDFs
- Type Juggling & Magic Hashes
- Blind SQL Injection
- CSRF & REGEX Bypasses
- .NET Assembly Debugging